Cybersecurity trends and challenges according to the latest Neustar report

The ever-changing cybersecurity landscape has become a real challenge for businesses recently.
With hackers getting more sophisticated and business minded day by day, cyber-attacks have turned into a money-maker for ‘underground’ corporations.
Learn more about cyber security trends and what we could expect from the ‘bad guys’ according to the latest report from Neustar – a leading security services provider who are also the registry behind the .US domain extension and whom we have accreditation with.
What are cyber-attacks about?
Neustar launched their cybersecurity report with one basic goal in mind – to raise awareness about the ever-changing threats on the web.

It has become evident that cyber criminals have started to change their tactics over recent years.
In the past the main goal of an attacker was to disrupt a service, now their main goal is to outsmart the system.
Web-based attacks like DDoS attacks, for example, used to be the main-stage show, now they are just a smokescreen for the real scenario.
Today’s cyber-attacks have become more targeted and well-conceived.
In fact, attackers now no longer need any specific skills or infrastructure to launch an attack.
They can simply buy the malware code they need and rent the necessary equipment (like botnets) online.

This gives criminals peace of mind and plenty of time to focus on the results they pursue.
James Willett, a cyber security expert at Neustar, has recently said in an interview that “within five minutes, you can be sending a denial of service attack to any organization in the world.”
It looks like cybercrime has turned into a corporation with each criminal having their own specialization in making money off security glitches.
Namely for that reason, recent cyber-attacks have become much more sophisticated and hard to detect.

Back in 2016 cyber-attacks were volumetric and aimed at taking companies offline with a splash, this year security experts have been faced with multi-stage scenarios that are really hard to detect until they hit you.
So far in 2018 DDoS attacks are following a different pattern – they start out small and are first used as a means of scouting and espionage.
Then they can quickly grow into multi-vector attacks, which empowers attackers to sneak into wherever they want.
For instance, in a recent incident, Neustar stopped a ‘quantum’ attack of just 300 MBps, which in fact featured 15 different attack vectors and was using protocols to circumvent the company’s defence system.
Also, Neustar recently thwarted the first IPv6 attack in history and their prediction is that the number of such attacks is yet to explode due to the growing adoption of the new IP standard.
This is why security experts and organizations need to keep in mind that they have a really powerful arsenal of weapons to deal with.
The most significant types of cyber-attacks involve malware and data breaches.
In their cyber report Neustar provide a rundown of the most prevalent security threats and go into detail about their most prominent features.
Here is a list of the most noteworthy of them:
Ransomware
With an annual growth rate of 350% (Cisco’s Annual Cybersecurity Report), ransomware attacks have been recognized as a global security issue at the 2018 World Economic Forum.
The modern age of ransomware started with CryptoLocker in 2013 and developed into real global disasters like WannaCry, which affected 300 000 computers across 150 countries, and NotPetya which caused quarterly losses of US$300 million for a number of companies.
Ransomware is a type of malware that attackers use to take over a computer or network and then demand a ransom from the owner, promising to restore access to the data upon payment.
It can access a computer via phishing spam attachment files or security hole exploits.
Botnets
Botnets were originally intended for legitimate purposes only like site indexing, data aggregation, online trading, etc.
However, their capabilities may very well be employed for launching destructive campaigns like DDos attacks, spamming, phishing, traffic sniffing and many more.
Botnet-based malware is targeted at IoT devices which are ON most of the time and are used with low security precautions. Also, this malware uses infected devices as a means for scanning other vulnerable targets.
Some of the most prominent botnets include:
– Mirai, which inflicted a large-scale disruption in 2016 by shutting down the site of a security guru and by targeting a large DNS provider. It generated over 1 Tbps of traffic and featured 10 pre-defined attack vectors.
– WireX, which targeted a number of CDN providers in a volumetric DDoS attack via a network of malicious-app-running Android devices from over 100 countries.
DDoS Attacks
According to Kaspersky Labs, the rate of businesses hit by DDoS attacks has doubled (from 17% in 2016 to 33.4% in 2017). The number of companies hit more than once has increased as well.
DDoS attacks can be of various sizes and can be launched for any reason you could imagine such as:
• exhausting the bandwidth of a site or network (volumetric attacks);
• exhausting the number of concurrent sessions that a web server, a firewall or a load balancer could handle (protocol attacks);
• overwhelming specific applications like DNS services with HTTP(S) requests (application layer attacks);
Reflection and Amplification Attacks
According to 2018’s annual cybersecurity report of Cisco, application attacks, reflection & amplification attacks in particular, have managed to overtake network DDoS attacks.
Such attacks provide virtually no warning and are much more difficult to detect than DDoS attacks.
This ‘stealthiness’ allows criminals to make a vulnerability assessment of web applications at ease and increases the risk of irreversible consequences.
Reflection and amplification attacks allow hackers to spoof a target’s IP address and send a small query to a server, which in return could prompt a very large response to the target.
The majority of such attacks target services that use a protocol such as UDP, which does not validate the source IP address.
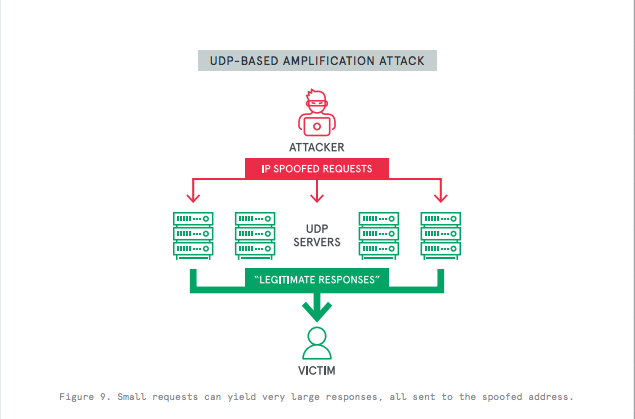
The most prominent reflection and amplification attack so far has been the Memcached amplification attack.
Memcached – an open-source, distributed memory caching system for speeding up web applications, mainly uses the UDP protocol, which has made it really easy for criminals to hack.
The recent Memcached attack was initiated with a 15 KB query which, due to the high-transit-connectivity network where Memcached machines are located, prompted a reply of more than 1500 KB.
Depending on the techniques used, amplification attacks could be used for injecting a malicious script into a web application, for tricking users into transferring funds or for changing email addresses on an infected application, etc.
According to Neustar’s report the majority of companies recognize Memcached attacks as a potential norm and have taken measures to strengthen their defence systems.
IPv6 Attacks
With IPv4 addresses being exhausted in many regions of the world, the IPv6 standard adoption rate has been increasing steadily.
The transition period for companies where the existing (IPv4) and the new (IPv6) networks are running in parallel, however, has been compromised by inconsistency in security standards.
This has allowed attackers to bypass firewalls and intrusion prevention systems and generate malicious traffic, which could not be recognized by IPv4 defences.
IPv6 addresses could also be used for DNS amplification attacks which make use of the DNS configuration differences between the IPv4 and IPv6 standards.
In a recent DNS server attack, involving devices from 1900 IPv6 addresses, 400 of the addresses were used by poorly configured DNS systems.
According to experts, these kind of attacks are expected to become an enormous problem in the future.
Cybersecurity recommendations by experts
With the explosion of IoT devices and the growing accessibility of hacking equipment and ready-made malware, the internet has turned into a fertile ground for cybercrime.
The scenarios in which the security of individuals or organizations could be compromised are evolving every day.
For example, almost every modern device and PC has IPv6 included and turned on by default, which leaves the door open to IPv6 attacks.
Today, the very fact that you are online makes you susceptible to an attack. So the question is not if you will be attacked, but when.
Also, organizations often take measures to protect against a single type of threat but the truth is that attacks are getting more complex and rarely occur in isolation.
At the same time, cyber experts are faced with an ever-growing army of anonymous attackers who are no longer required to be well-trained ‘fighters’ in order to launch a devastating attack.
Now they can simply rent a botnet and purchase the necessary application exploit, investing all of their efforts and time on creating the perfect malicious scenario.
For this reason, organizations need to think of adopting a wholesome and comprehensive security strategy that will help them save their online reputation.
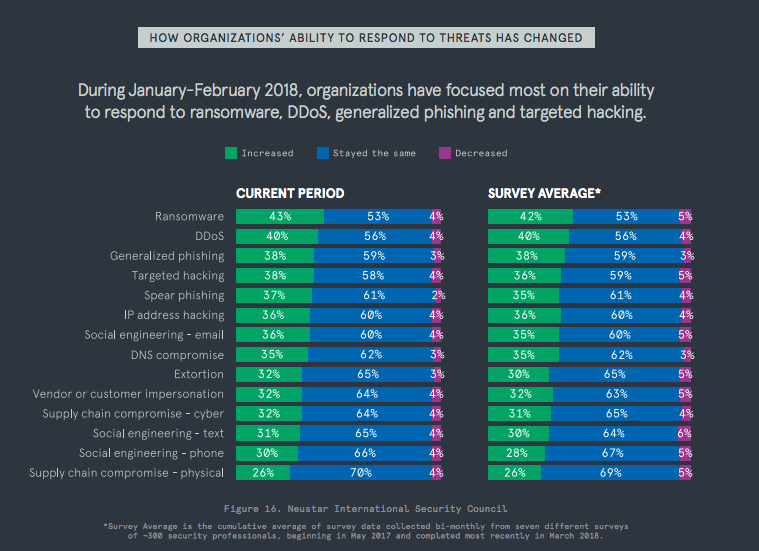
For instance, the combined use of WAF and DDoS mitigation systems from the same provider often provides a more efficient and comprehensive defence, according to the cyber security specialists at Neustar.
You can read the full report on Neustar’s website after filling out a short signup form.
Originally published Thursday, September 6th, 2018 at 5:10 pm, updated July 8, 2024 and is filed under Online Security.Tags: online security, Memcached, online

