A new Lilocked (Lilu) ransomware infects thousands of servers. We are patched!

A new ransomware has recently been detected to be exclusively targeting Linux-based servers.
The so-called Lilocked (or Lilu) ransomware has been intensively infecting thousands of servers for a couple of weeks now.
We are glad to inform you that our servers are patched and your content is immune to infection.
Learn more about the nature and scope of the Lilocked (Lilu) ransomware.
What is the Lilocked (or Lilu) ransomware about?
Currently, it looks like the Lilocked ransomware is targeting Linux-based systems only.
The way Lilocked acts is to gain root access to servers and encrypt specific file types (like HTML, JS, CSS, PHP, and various image files).
Since no system files are affected (which may be regarded as the lesser evil), an infected server would continue to run normally, without its owner realizing it has been hit.
An infected server can be recognized in that the majority of the files it hosts are encrypted and have a new “.lilocked” extension:
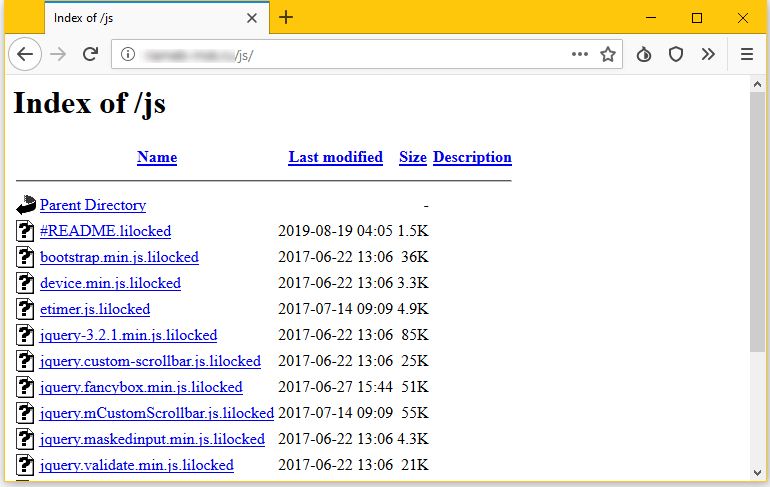
The ransomware also leaves a #README.lilocked note in each folder with encrypted files instructing affected users to access a certain website and pay a ransom to have their files decrypted:
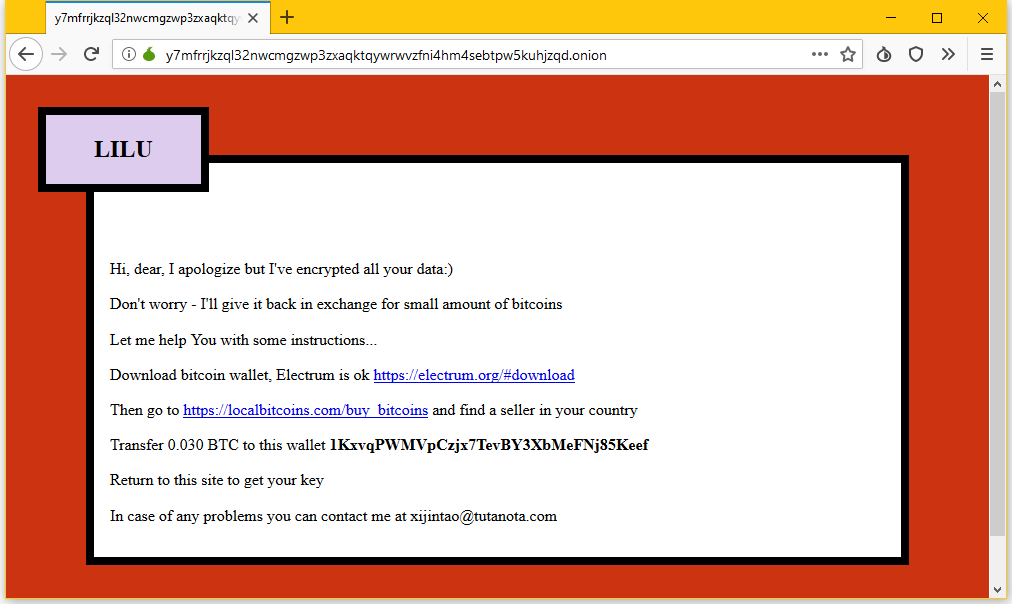
The first reports of the Lilocked infection came in mid-July when some victims uploaded their ransom note on a website for ransomware identification.
However, it was not until recently that Lilocked was detected by security researchers due to the rapidly increasing number of affected Linux-based servers.
Most of the infected websites on those servers have been indexed and cached in Google search results which means that their trust factor has been compromised.
What are the security measures needed to avoid Lilocked infection?
According to specialists, systems running an outdated version of the Exim (email) software might be most vulnerable to Lilocked infection.
However, this is just a hypothesis that is yet to be confirmed.
For now, specialists can only give generic security advice to server owners i.e. to avoid opening suspicious or unknown links and files, only download software from official sources, keep applications up to date with security patches, and use unique passwords for their accounts.
As mentioned earlier in the post, all servers across our platform are patched against the Lilocked infection so you can rest assured that your data is safe with us.
Originally published Tuesday, September 10th, 2019 at 1:06 pm, updated September 18, 2019 and is filed under Online Security.

Leave a Reply